IT Crash Course Day 3: Virtualization, Cloud Computing, and Infrastructure Management
Table of Contents
- VMware Virtualization
- Cloud Computing Concepts
- Azure Active Directory and Microsoft Intune
- On-Premises Infrastructure Management
- Career Insights for Hybrid Environment Support
VMware Virtualization
Introduction to Virtualization and Hypervisors
Virtualization is a technology that abstracts physical hardware resources to create multiple virtual systems on a single physical machine. It enables more efficient use of computing resources by allowing multiple operating systems to run simultaneously on one physical server.
Benefits of Virtualization:
- Resource efficiency: Higher utilization of physical hardware
- Isolation: Applications run in separate environments
- Flexibility: Easy provisioning and decommissioning of virtual environments
- Hardware independence: Virtual machines run regardless of underlying hardware
- Disaster recovery: Simplified backup and recovery processes
Hypervisor Types:
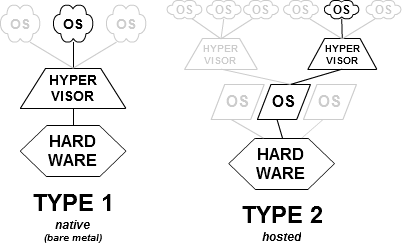
A hypervisor is software that creates and manages virtual machines. There are two main types:
Type 1 (Bare-metal) Hypervisors:
- Install directly on hardware without an underlying OS
- More efficient and secure
- Better performance with less overhead
- Examples: VMware ESXi, Microsoft Hyper-V, Citrix Hypervisor (formerly XenServer)
- Used primarily in enterprise environments
Type 2 (Hosted) Hypervisors:
- Run on top of a conventional operating system
- Easier to set up but less efficient
- Examples: VMware Workstation, Oracle VirtualBox, Parallels Desktop
- Used primarily for development, testing, and desktop virtualization
Virtualization Terminology:
- Host: The physical machine running the hypervisor
- Guest: The virtual machine running on the hypervisor
- Virtual Machine (VM): A software-based computer that runs like a physical computer
- Virtual Hardware: Software components that act like physical hardware
- VM Image: A file representing a virtual machine's state
VMware vSphere Ecosystem
VMware vSphere is a comprehensive virtualization platform that includes multiple components working together to provide enterprise virtualization capabilities.
Core Components:
VMware ESXi:
- Type 1 hypervisor installed directly on physical hardware
- Provides computing and memory resources to VMs
- Handles hardware abstraction
- Manages VM execution
- Minimal footprint with just enough operating system to run VMs
VMware vCenter Server:
- Centralized management platform for ESXi hosts
- Enables features like vMotion, DRS, and HA
- Provides a single point of administration for all hosts and VMs
- Handles authentication, permissions, and role assignments
- Available as a virtual appliance or Windows installation

Additional vSphere Components:
vSphere Client:
- HTML5-based web interface for managing vSphere environment
- Access to virtual machines, hosts, and vCenter features
vSphere Distributed Switch (vDS):
- Centralized management of network configuration across multiple hosts
vSphere Distributed Resource Scheduler (DRS):
- Automatically balances VM workloads across hosts
vSphere High Availability (HA):
- Restarts VMs on different hosts if a host fails
vSphere Fault Tolerance (FT):
- Provides continuous availability for VMs by creating mirrored instances
vSAN (Virtual Storage Area Network):
- Software-defined storage solution that pools direct-attached storage
vSphere Environment Structure:
vCenter Server
├── Data Center
│ ├── Cluster
│ │ ├── ESXi Host 1
│ │ │ ├── VM 1
│ │ │ ├── VM 2
│ │ ├── ESXi Host 2
│ │ │ ├── VM 3
│ │ │ ├── VM 4
│ ├── Resource Pool
│ ├── Datastores
│ ├── Networking
Virtual Machine Creation and Configuration
VM Creation Process:
- Select Create/Register VM in vSphere Client
- Choose creation type:
- Create new VM
- Deploy from template
- Clone existing VM
- Deploy from OVF/OVA
- Select a name and location for the VM
- Choose compute resource (host/cluster)
- Select storage (datastore)
- Choose compatibility (VM hardware version)
- Select guest OS (Windows, Linux, etc.)
- Customize hardware:
- CPU
- Memory
- Hard disk
- Network adapter
- CD/DVD
- USB controller
- Review and finish
VM Resource Allocation:
vCPU Configuration:
- Socket count: Number of virtual CPU sockets
- Cores per socket: CPU cores per socket
- Resource allocation: Shares, reservations, and limits
- Hot-add: Enable/disable CPU hot-add
Memory Configuration:
- RAM allocation: Total virtual memory assigned to VM
- Memory overhead: Additional memory required for virtualization
- Memory reservation: Guaranteed minimum allocation
- Memory limit: Maximum allocation
- Memory shares: Priority for memory allocation
Storage Configuration:
- Virtual disk types:
- Thin provisioned: Allocates storage on demand
- Thick provisioned lazy zeroed: Allocates all storage immediately
- Thick provisioned eager zeroed: Allocates and zeroes all storage (best performance)
- Virtual disk sharing options
- Disk controller types (IDE, SCSI, SATA, NVMe)
Network Configuration:
- Network adapter types (E1000, VMXNET3)
- Connection to port groups
- MAC address assignment
- Traffic shaping

VM Configuration Best Practices:
- Align virtual hardware with actual needs
- Use paravirtualized drivers when available (VMXNET3, PVSCSI)
- Disable unnecessary virtual hardware
- Install VMware Tools in every VM
- Follow vendor recommendations for guest OS
- Monitor resource utilization and adjust as needed
Key VMware Concepts
Snapshots:
- Point-in-time capture of VM state
- Includes memory state, VM settings, and disk state
- Uses delta disks to track changes since snapshot
- Use cases:
- Before software/patch installation
- Testing configuration changes
- Creating development/test environments
- Limitations:
- Not a backup replacement
- Performance impact if left for extended periods
- Disk space requirements
- Maximum of 32 snapshots in a chain

Cloning:
- Creates an exact copy of an existing VM
- Results in a new, independent VM
- Types:
- Full clone: Complete copy, independent of parent
- Linked clone: Shares virtual disks with parent VM, stores only differences
- Use cases:
- Deploying multiple similar VMs
- Creating test environments
- Preserving master images
Templates:
- Master copy of a VM used as a standardized image for deployment
- Cannot be powered on directly
- Maintains integrity of the master image
- Advantages:
- Standardization across deployments
- Time savings for repetitive deployments
- Consistency in configuration
- Process:
- Convert VM to template
- Deploy new VMs from template
- Customize during deployment (hostname, IP, etc.)
vMotion:
- Live migration of running VMs between hosts with no downtime
- Transfers VM memory, state, and storage if needed
- Types:
- vMotion: Migrates VM compute (CPU/memory)
- Storage vMotion: Migrates VM storage while VM is running
- Requirements:
- Shared storage (for standard vMotion)
- Compatible CPU families between hosts
- Sufficient network bandwidth
- Network connectivity between source and destination
- Use cases:
- Load balancing
- Hardware maintenance
- Host evacuation
- Storage maintenance

VMware Tools:
- Suite of utilities and drivers for guest operating systems
- Key features:
- Enhanced graphics performance
- Unity mode for seamless application display
- Shared folders between host and guest
- Time synchronization
- Automated scripts for VM lifecycle
- Improved mouse performance
- Heartbeat capability for HA
- Should always be installed and kept updated in guest OS
Knowledge Check: VMware Virtualization
-
What is the primary difference between Type 1 and Type 2 hypervisors? a) Type 1 supports more virtual machines than Type 2 b) Type 1 runs directly on hardware while Type 2 runs on a host OS c) Type 1 is used for servers while Type 2 is used for desktop virtualization only d) Type 1 supports Windows VMs while Type 2 supports Linux VMs
-
Which component in the vSphere ecosystem provides centralized management of multiple ESXi hosts? a) vMotion b) vSAN c) vCenter Server d) vSphere Client
-
What is the primary purpose of VMware snapshots? a) To create permanent backups of virtual machines b) To capture point-in-time states that can be reverted to later c) To migrate VMs between hosts d) To convert physical servers to virtual machines
-
Which vSphere feature allows a running virtual machine to be moved from one physical host to another with no downtime? a) High Availability b) Fault Tolerance c) vMotion d) Clone
-
When creating a virtual disk for a VM, what is the difference between thin and thick provisioning? a) Thin provisioned disks are faster than thick provisioned disks b) Thin provisioning allocates all storage space immediately while thick provisioning allocates on demand c) Thin provisioning allocates storage space on demand while thick provisioning allocates all space immediately d) Thick provisioning allows for disk sharing while thin provisioning does not
Cloud Computing Concepts
Core Concepts of Cloud Computing
Cloud Computing Definition: Cloud computing is the on-demand delivery of computing resources—including servers, storage, databases, networking, software, and analytics—over the internet, typically with pay-as-you-go pricing.
Essential Characteristics (NIST Definition):
- On-demand self-service: Resources available when needed without human intervention
- Broad network access: Capabilities available over network using standard mechanisms
- Resource pooling: Provider resources serve multiple consumers using multi-tenancy
- Rapid elasticity: Capabilities scale quickly in and out based on demand
- Measured service: Resource usage monitored, controlled, and reported transparently
Enabling Technologies:
- Virtualization: Foundation of cloud computing that separates physical infrastructure from computing services
- Automation: Enables rapid provisioning and scaling of resources
- High-speed networks: Facilitate access to cloud resources
- APIs: Allow programmatic access and management of cloud resources
- Containerization: Lightweight alternative to full virtualization

Cloud Deployment Models
Public Cloud:
- Computing services offered by third-party providers over the internet
- Resources shared among multiple organizations
- Characteristics:
- No capital expenditure required
- Pay-for-what-you-use pricing
- Provider handles maintenance
- Generally more cost-effective at scale
- Limited customization
- Examples: Amazon Web Services (AWS), Microsoft Azure, Google Cloud Platform (GCP)
- Ideal for: Web applications, development/test environments, applications with variable workloads
Private Cloud:
- Dedicated cloud environment for a single organization
- Can be on-premises or provider-hosted
- Characteristics:
- Enhanced control and security
- Customizable to organization needs
- Potentially higher costs
- Organization manages infrastructure (or pays provider)
- Compliance advantages for regulated industries
- Examples: VMware vCloud, OpenStack, Microsoft Azure Stack
- Ideal for: Financial institutions, government agencies, healthcare organizations
Hybrid Cloud:
- Mix of public and private clouds with orchestration between platforms
- Characteristics:
- Flexibility to run workloads in optimal environment
- Cost optimization (capital + operational expenses)
- Allows for gradual cloud migration
- Can be complex to manage
- Requires compatible architectures
- Example scenarios: Burst capacity to public cloud, keep sensitive data on-premises
- Ideal for: Enterprises with existing infrastructure investments, organizations with variable workloads
Multi-Cloud:
- Using services from multiple cloud providers
- Characteristics:
- Avoids vendor lock-in
- Uses best services from each provider
- Geographic distribution
- Complex management and security
- Example: Using AWS for compute, Azure for Office 365, and GCP for machine learning

Cloud Service Models
Infrastructure as a Service (IaaS):
- Provides virtualized computing resources
- Customer manages OS, middleware, applications
- Key components:
- Virtual machines
- Storage
- Networks
- Load balancers
- Characteristics:
- Most flexibility
- Most customer responsibility
- Similar to traditional IT but as a service
- Examples: AWS EC2, Azure Virtual Machines, Google Compute Engine
- Use cases: Lift-and-shift migrations, test/dev environments, web apps
Platform as a Service (PaaS):
- Provides platform for developing, running, and managing applications
- Provider manages underlying infrastructure
- Key components:
- Runtime environments
- Development tools
- Database services
- Application services
- Characteristics:
- Focus on application development
- Reduced operational burden
- Often includes auto-scaling
- May have language/framework limitations
- Examples: Azure App Service, Google App Engine, AWS Elastic Beanstalk
- Use cases: API development, web applications, IoT applications
Software as a Service (SaaS):
- Complete applications delivered over the internet
- Subscription-based access
- Characteristics:
- Minimal customer management
- Automatic updates
- Accessible from anywhere
- Multi-tenancy
- User-based pricing common
- Examples: Microsoft 365, Salesforce, Google Workspace, Dropbox
- Use cases: Email, collaboration, CRM, office applications

Emerging Service Models:
Function as a Service (FaaS)/Serverless:
- Event-driven execution model
- Runs code in stateless containers
- Pay only for execution time
- Examples: AWS Lambda, Azure Functions, Google Cloud Functions
Container as a Service (CaaS):
- Managed container orchestration
- Examples: Azure Container Instances, AWS ECS, Google Kubernetes Engine
Benefits and Challenges of Cloud Computing
Benefits:
Cost Efficiency:
- Shift from capital expenditure (CapEx) to operational expenditure (OpEx)
- Pay-as-you-go pricing
- Reduced infrastructure maintenance costs
- No need to account for peak capacity in purchases
- Lower total cost of ownership
Scalability and Elasticity:
- Scale resources up or down based on demand
- Rapid provisioning of new resources
- Handle unexpected traffic spikes
- Seasonal scaling without overprovisioning
- Auto-scaling capabilities
Reliability and Availability:
- Geographical redundancy
- Built-in backup and disaster recovery
- Service level agreements (SLAs)
- Reduced single points of failure
- High availability architectures
Agility and Innovation:
- Faster deployment of new services
- Quick experimentation and prototyping
- Access to latest technologies
- Focus on business value rather than infrastructure
- Faster time to market
Global Reach:
- Deploy applications closer to users worldwide
- Consistent experience regardless of location
- Edge locations reduce latency
- Global infrastructure without global investment
Challenges:
Security and Compliance:
- Shared responsibility model
- Data sovereignty concerns
- Regulatory compliance across regions
- Security control limitations
- Third-party risk management
- Public internet exposure
Performance and Latency:
- Dependency on internet connectivity
- Possible performance variability
- Bandwidth limitations
- Distance from cloud regions
- Noisy neighbor problems
Cost Management:
- Unexpected costs from scaling
- Complex pricing models
- Resource waste if not monitored
- Bandwidth and data transfer costs
- Lock-in concerns affecting cost negotiation
Skills Gap:
- Need for cloud-specific expertise
- Evolving technologies require continuous learning
- Managing hybrid environments
- Multi-cloud complexity

IT Support Perspective:
Support Challenges:
- Troubleshooting hybrid environments
- Limited visibility into cloud infrastructure
- Managing access controls across environments
- Vendor support coordination
- Keeping up with rapid service changes
Support Opportunities:
- Automation of routine tasks
- Enhanced monitoring tools
- Self-service capabilities
- Proactive issue detection
- Focus on strategic initiatives
Knowledge Check: Cloud Computing
-
Which of the following is NOT one of the five essential characteristics of cloud computing according to NIST? a) On-demand self-service b) Broad network access c) Physical hardware control d) Measured service
-
In which cloud deployment model would an organization maintain complete control over their infrastructure while still utilizing cloud technologies? a) Public cloud b) Private cloud c) Hybrid cloud d) Multi-cloud
-
Which cloud service model requires customers to manage the operating system and applications but not the underlying hardware? a) SaaS b) PaaS c) IaaS d) FaaS
-
What is the primary benefit of a hybrid cloud approach? a) Reduced security concerns b) Simplified management c) Flexibility to run workloads in the optimal environment d) Lower costs in all scenarios
-
From an IT support perspective, which of the following represents a significant challenge when supporting cloud environments? a) Reduced need for security monitoring b) Limited visibility into cloud infrastructure c) Elimination of hardware failures d) Simplified user access management
Azure Active Directory and Microsoft Intune
Azure Active Directory Overview
Azure Active Directory (Azure AD) is Microsoft's cloud-based identity and access management service. It's the backbone of the Microsoft 365 ecosystem and provides authentication for various cloud services.
Key Differences from On-Premises AD:
| Feature | Azure Active Directory | On-Premises Active Directory |
|---|---|---|
| Primary Focus | Web-based applications | Windows domain environment |
| Authentication | Modern auth protocols (OAuth, SAML) | Kerberos and NTLM |
| Structure | Flat structure with users and groups | Hierarchical with OUs and domains |
| Management | Portal and PowerShell | MMC snap-ins, PowerShell |
| Devices | Modern device management | Group Policy management |
Azure AD Editions:
- Free: Basic user and group management
- Office 365 Apps: Included with Microsoft 365
- Premium P1: Hybrid identities, advanced group features
- Premium P2: Identity protection and privileged identity management
Core Functionality:
- Authentication: Verifying user identity
- Authorization: Determining access permissions
- Single Sign-On (SSO): One login for multiple applications
- Multi-Factor Authentication (MFA): Enhanced security beyond passwords
- Conditional Access: Context-based access policies
- Identity Protection: Risk-based security
- Application Management: Managing access to enterprise applications

Azure AD Architecture:
Azure AD Tenant
├── Users
│ └── User attributes
├── Groups
│ ├── Security Groups
│ └── Microsoft 365 Groups
├── Applications
│ ├── Enterprise applications
│ └── App registrations
├── Devices
│ ├── Azure AD joined
│ ├── Hybrid joined
│ └── Azure AD registered
└── Conditional Access Policies
Azure AD Connect:
- Synchronization tool between on-premises AD and Azure AD
- Enables hybrid identity scenarios
- Synchronizes users, groups, and attributes
- Password hash synchronization or pass-through authentication
- Enables single sign-on between on-premises and cloud
User and Group Management in Azure AD
User Management:
User Types:
- Cloud identities: Created directly in Azure AD
- Synchronized identities: Synced from on-premises AD
- Guest users: External users invited to access resources
User Lifecycle Management:
- Provisioning: Creating user accounts
- Manual creation
- Bulk operations
- Automated provisioning from HR systems
- Updates: Maintaining accurate information
- Deprovisioning: Removing access when needed
User Properties:
- Profile information
- Job information
- Contact details
- Authentication methods
- Group memberships
- Application assignments
- License assignments

Group Management:
Group Types:
- Security Groups: Used for permission assignments
- Microsoft 365 Groups: Collaborative groups with shared resources
Group Membership Types:
- Assigned: Manually added members
- Dynamic User: Rules-based membership
- Dynamic Device: Rules-based for devices
Group Features:
- Nesting groups
- Self-service group management
- Usage and activity reports
- Expiration policies
- Naming policies
Administrative Units:
- Container for users, groups, and devices
- Delegate administrative permissions
- Scope administrative actions
Role-Based Access Control (RBAC):
- Built-in roles: Pre-defined permission sets
- Custom roles: Tailored permission sets
- Privileged Identity Management (PIM): Just-in-time role activation

Authentication Management:
Password Policies:
- Complexity requirements
- Expiration policies
- Password protection
Multi-Factor Authentication (MFA):
- Something you know (password)
- Something you have (phone, token)
- Something you are (biometric)
Self-Service Password Reset (SSPR):
- User-initiated password resets
- Multiple verification methods
- On-premises writeback
Microsoft Intune
Microsoft Intune is a cloud-based mobile device management (MDM) and mobile application management (MAM) service that helps organizations manage devices and applications.
Core Capabilities:
Device Management:
- Configure device settings
- Assess device compliance
- Provision devices with certificates
- Update operating systems
- Reset or remotely wipe devices
Application Management:
- Deploy and configure apps
- Control app data
- Remove organizational data from apps
- Update apps
- Report on app inventory
Policy Management:
- Create and assign policies
- Monitor policy compliance
- Remediate policy violations
- Integrate with conditional access

Intune Architecture:
Microsoft Intune
├── Devices
│ ├── Windows 10/11
│ ├── iOS/iPadOS
│ ├── Android
│ └── macOS
├── Apps
│ ├── Store apps
│ ├── Line-of-business apps
│ ├── Web apps
│ └── Office apps
├── Policies
│ ├── Configuration profiles
│ ├── Compliance policies
│ ├── App protection policies
│ └── Security baselines
└── Conditional Access
└── (Integration with Azure AD)
Supported Platforms:
- Windows 10/11
- iOS/iPadOS
- Android
- macOS
Intune vs. Traditional Management:
| Feature | Intune (Modern) | Traditional Management |
|---|---|---|
| Infrastructure | Cloud-based | On-premises servers |
| Management reach | Any internet connection | Corporate network |
| Device types | Multiple platforms | Primarily Windows |
| Updates | Automatic service updates | Manual infrastructure updates |
| Integration | Cloud services | Mainly on-premises services |
Integration Points:
- Azure AD: Identity and conditional access
- Microsoft 365: App protection for Office apps
- Endpoint Manager: Unified management interface
- Microsoft Defender for Endpoint: Threat protection
Device Enrollment and Policy Deployment
Enrollment Methods:
User-Driven Enrollment:
- Self-service enrollment by end users
- Company Portal app installation
- Email instructions
- Best for BYOD scenarios
Admin-Driven Enrollment:
- Apple Business Manager/Apple School Manager: iOS/iPadOS devices
- Android Enterprise: Android devices
- Windows Autopilot: Windows devices
- Bulk enrollment: Multiple devices at once
Enrollment Process Flow:
-
Preparation:
- Configure Intune policies
- Set up enrollment restrictions
- Create enrollment profiles
-
Device Registration:
- Register device with appropriate platform service
- Associate with organization account
-
Enrollment:
- User or admin initiates enrollment
- Authentication to Azure AD
- MDM profile installation
- Certificate provisioning
-
Configuration:
- Policy application
- App installation
- Setting configuration
- Security validation

Policy Types:
Device Configuration Profiles:
- Operating system settings
- Device features
- Device restrictions
- Endpoint protection
- Custom settings
Compliance Policies:
- Minimum OS versions
- Password requirements
- Encryption status
- Jailbreak/root detection
- Secure boot status
App Protection Policies:
- Data protection without device enrollment
- App-level settings
- Data sharing restrictions
- Save-as controls
- PIN requirements
Security Baselines:
- Pre-configured groups of settings
- Industry best practices
- Microsoft-recommended configurations
- Simplified security implementation
Policy Assignment:
- Assigned to users or devices
- Group-based targeting
- Include and exclude groups
- Assignment filters for granular targeting
Monitoring and Reporting:
- Device status
- Policy status
- Application inventory
- Enrollment status
- Compliance reports
- Detected risks

Troubleshooting Tools:
- Device details view
- Policy evaluation logs
- Tenant status page
- Enrollment failure reports
- Intune data warehouse
Knowledge Check: Azure AD and Intune
-
What is the primary difference between Azure Active Directory and traditional on-premises Active Directory? a) Azure AD cannot store user accounts b) Azure AD focuses on web-based applications while on-premises AD focuses on Windows domain services c) Azure AD doesn't support groups d) On-premises AD is more secure by design
-
Which Azure AD feature allows organizations to enforce additional verification steps based on user location, device status, and risk level? a) Multi-Factor Authentication b) Conditional Access c) Azure AD Connect d) Self-Service Password Reset
-
Which type of policy in Microsoft Intune evaluates whether a device meets organizational security requirements? a) Configuration profile b) App protection policy c) Compliance policy d) Enrollment restriction
-
What is the primary advantage of using App Protection Policies in Intune? a) They can completely restrict access to device hardware b) They can protect organization data at the application level without requiring device enrollment c) They can automatically install all required applications d) They are only available for iOS devices
-
In a hybrid identity scenario, what tool synchronizes users between on-premises Active Directory and Azure AD? a) Azure AD Connect b) Microsoft Intune c) Endpoint Manager d) Group Policy Management
On-Premises Infrastructure Management
Domain Controllers
Domain Controller Definition: A domain controller (DC) is a server that responds to authentication requests and verifies users on computer networks. It's a central component of Active Directory Domain Services.
Key Functions:
- Authenticate users and computers
- Store directory data
- Replicate with other domain controllers
- Process login requests
- Enforce security policies
- Provide DNS services (typically)
Domain Controller Types:
Primary Domain Controller (PDC) Emulator:
- One per domain
- Manages password changes
- Acts as time source
- Handles authentication requests
- Processes Group Policy Objects
Additional Domain Controllers:
- Provide authentication redundancy
- Reduce authentication traffic over WAN
- Improve login times for remote sites
- Enable high availability
Read-Only Domain Controllers (RODCs):
- Contain read-only copy of AD database
- Cannot process password changes
- Ideal for less secure locations
- Limited replication

Physical vs. Virtual Domain Controllers:
| Aspect | Physical DCs | Virtual DCs |
|---|---|---|
| Performance | Dedicated hardware | Shared resources |
| Recovery | Hardware replacement needed | Easy VM restoration |
| Portability | Limited | Can be moved between hosts |
| Cost | Higher hardware costs | Better hardware utilization |
| Snapshot risks | N/A | USN rollback concerns |
Domain Controller Placement:
- At least two DCs per domain for redundancy
- Strategic placement in physical locations
- Consider network topology
- Plan for disaster recovery sites
Monitoring Domain Controllers:
- Replication status
- CPU and memory utilization
- Disk space
- Event logs for errors
- DCDIAG tool for diagnostics
Active Directory Concepts
Active Directory Domain Services (AD DS) is Microsoft's directory service for Windows domain networks.
Core Components:
Domains:
- Primary unit of logical structure
- Security boundary
- Sharing common directory database
- Identified by DNS name (example.com)
Trees:
- Hierarchy of domains sharing contiguous namespace
- Child domains automatically trust parent domains
- Example: corp.example.com is child of example.com
Forests:
- Collection of one or more trees
- Share schema and configuration
- Connect via two-way transitive trusts
- Highest security boundary

Physical Components:
Sites:
- Represent physical network topology
- Based on IP subnets
- Used for authentication and replication
- Not visible to end users
Domain Controllers:
- Servers running AD DS role
- Store and replicate directory data
- Process authentication requests
Directory Database:
- Ntds.dit file
- Contains all AD objects and attributes
- Stored on domain controllers
- Replicated between DCs
Logical Components:
Objects:
- Users, computers, groups, printers, etc.
- Have distinct attributes
- Globally unique identifiers
Organizational Units (OUs):
- Container objects for organizing other objects
- Hierarchical structure
- Delegation of administration
- Group Policy application
- Does NOT affect security (unlike domains)

Users and Computers:
- User objects represent people or services
- Computer objects represent workstations and servers
- Must be authenticated to access domain resources
- Managed through Active Directory Users and Computers
Groups:
- Collection of users, computers, and other groups
- Used for access control and email distribution
- Security Groups: Used for permissions
- Distribution Groups: Used for email only
Group Scopes:
- Domain Local: Permissions within one domain
- Global: Members from own domain, used anywhere in forest
- Universal: Members from any domain, used anywhere in forest
Group Nesting Best Practices:
- Global groups contain users
- Domain Local groups contain Global groups
- Domain Local groups assigned permissions
- "AGDLP" principle (Account → Global → Domain Local → Permission)
Active Directory Database:
- Partitioned structure
- Schema Partition: Object definitions
- Configuration Partition: Forest-wide settings
- Domain Partition: Domain-specific data
- Replicated based on partition type
Group Policy Objects (GPOs)
Group Policy is a feature of Active Directory that provides centralized management and configuration of operating systems, applications, and users' settings.
Group Policy Components:
Group Policy Objects (GPOs):
- Collection of settings applied to users and computers
- Stored in the Group Policy Container (GPC) in AD
- Settings stored in Group Policy Template (GPT) on SYSVOL
- Linked to domains, sites, or OUs
Group Policy Management Console (GPMC):
- Tool for managing GPOs
- Creating, editing, and linking GPOs
- Backup and restore functionality
- Results and modeling tools
Group Policy Editor:
- Interface for configuring GPO settings
- Accessed through GPMC
- Organized in Computer and User Configuration
- Policies vs. Preferences distinction

GPO Processing:
- Local Group Policy
- Site-linked GPOs
- Domain-linked GPOs
- OU-linked GPOs (parent to child)
GPO Application Rules:
- Multiple GPOs processed in sequence
- Later GPOs override earlier ones (with exceptions)
- Enforced GPOs take precedence
- Block inheritance can prevent higher-level GPOs
- Loopback processing for special cases
GPO Filtering:
- Security filtering limits GPO scope
- WMI filtering applies GPOs based on system criteria
- Item-level targeting for preferences
Common GPO Settings:
Computer Configuration:
- Security settings
- Windows update configuration
- Startup/shutdown scripts
- Software installation
- Folder redirection
- Drive mappings
- Printer assignments
User Configuration:
- Desktop settings
- Start menu configuration
- Internet Explorer settings
- Mapped drives
- Application settings
- Logon/logoff scripts

GPO Troubleshooting Tools:
- gpresult: Shows applied GPOs
- GPUpdate: Forces GPO refresh
- Group Policy Results Wizard: Shows applied settings
- Group Policy Modeling Wizard: Simulates GPO application
GPO Best Practices:
- Use descriptive GPO names
- Create GPOs by function, not by OU
- Minimize the number of GPOs
- Use security filtering appropriately
- Test GPOs before deployment
- Document GPO purpose and settings
- Use comments within GPOs
User and NTFS Permissions
Windows Permission Types:
User Rights:
- Actions that users can perform on a system
- Configured through Group Policy
- Examples: Log on locally, Shut down the system
- Applied at the system level
NTFS Permissions:
- Control access to files and folders
- Applied to files/folders on NTFS formatted drives
- More granular than share permissions
- Persist regardless of access method
Share Permissions:
- Control network access to shared folders
- Three basic permissions: Read, Change, Full Control
- Applied only when accessing through network
- Combined with NTFS permissions (most restrictive wins)
NTFS vs. Share Permissions:
| Feature | NTFS Permissions | Share Permissions |
|---|---|---|
| Access control | File/folder level | Share level only |
| Permission granularity | Highly detailed | Basic (R/C/FC) |
| Applied when | Local and network access | Network access only |
| Persistence | Follows the file/folder | Only for network access |
| Configuration tool | File Explorer security tab | Sharing tab |
NTFS Basic Permissions:
- Read: View files and attributes
- Write: Create files and folders, write data
- Read & Execute: Read plus run programs
- List Folder Contents: View folder contents
- Modify: Read, write, execute, and delete
- Full Control: All permissions plus change permissions
NTFS Advanced Permissions:
- More granular control
- Examples: Traverse folder, Create files, Create folders
- Allows for precise permission assignments
- Combined to create basic permissions

Permission Assignment Process:
- Right-click file/folder
- Properties > Security tab
- Edit or Advanced button
- Add users/groups
- Assign appropriate permissions
- Apply changes
Permission Inheritance:
- Child objects inherit permissions from parent folders
- Can be disabled for specific folders/files
- "This folder, subfolders and files" option
- "Apply to" dropdown specifies inheritance scope
Special Permissions:
- Take Ownership: Ability to take ownership of objects
- Change Permissions: Ability to modify permissions
- Traverse Folder: Access files/folders without access to parent folders
- Delete Subfolders and Files: Allows deletion regardless of individual permissions
Permission Troubleshooting:
- Effective Access tab shows combined permissions
- Check both NTFS and Share permissions
- Consider group memberships
- Inheritance may override direct permissions
- "Deny" always overrides "Allow"

File and Folder Ownership:
- Owner has special rights to a file/folder
- By default, creator is the owner
- Administrators can take ownership
- Ownership can be transferred
- Critical for permission recovery scenarios
Knowledge Check: On-Premises Infrastructure
-
What is a primary function of a domain controller in Active Directory? a) Managing websites and web applications b) Authenticating users and computers in the domain c) Protecting against malware infections d) Optimizing network traffic routes
-
Which Active Directory component is used to logically group objects for easier management and policy application? a) Domains b) Trees c) Organizational Units (OUs) d) Sites
-
When multiple Group Policy Objects apply to a user or computer, what is the default processing order? a) Domain, Site, OU (parent to child) b) Local, Site, Domain, OU (parent to child) c) OU (child to parent), Domain, Site, Local d) Most recently created to oldest
-
What happens when both an "Allow" and a "Deny" NTFS permission are applied to the same user for the same file? a) Allow takes precedence b) Deny takes precedence c) The more recently applied permission wins d) The user receives an error message
-
What is the difference between Global and Universal groups in Active Directory? a) Global groups can only contain users from the same domain, while Universal groups can contain users from any domain in the forest b) Global groups apply to all domains, while Universal groups apply to one domain c) Global groups can contain only users, while Universal groups can contain users and computers d) Global groups are automatically replicated, while Universal groups must be manually synchronized
Career Insights for Hybrid Environment Support
As a technical support specialist in a hybrid environment, you'll need to understand both traditional on-premises infrastructure and modern cloud solutions. Here are some key insights for success:
Essential Skill Sets:
- Strong understanding of both on-premises and cloud technologies
- Ability to troubleshoot across environment boundaries
- Knowledge of identity management across platforms
- Security awareness for diverse technology stacks
- Adaptability as technologies evolve
Common Hybrid Support Scenarios:
- Identity synchronization issues: Troubleshooting Azure AD Connect
- Authentication problems: Users unable to access cloud resources
- Device management: Supporting both Intune and GPO managed devices
- Application access: On-premises vs. cloud application troubleshooting
- Security incidents: Coordinating response across environments
Daily Responsibilities:
- User account management across platforms
- Password reset support (on-premises and cloud)
- Device enrollment and configuration
- Application access and permission issues
- Security policy implementation and monitoring
Career Growth Paths:
- Cloud Administrator
- Systems Engineer
- Identity Management Specialist
- Security Operations Analyst
- Infrastructure Architect
Recommendations for Success:
- Obtain certifications in both on-premises and cloud technologies
- Build lab environments to practice hybrid scenarios
- Document common issues and their resolutions
- Develop automation skills for repetitive tasks
- Stay current with Microsoft's technology roadmap
Remember that hybrid environments are now the norm for most organizations, making your expertise in bridging these technologies extremely valuable.
This guide has provided a comprehensive overview of virtualization, cloud computing, and infrastructure management concepts essential for technical support specialists. By understanding these technologies and their interconnections, you'll be well-prepared to support modern IT environments and discuss these topics confidently in job interviews.
